Hong Kong protesters get pro bono cybersecurity help from Silicon Valley

American companies have for the most part spent the last week conspicuously putting their tails beneath their legs when faced with China’s economic might and the country’s willingness to censor critical opinions.
On Wednesday, an emphatic counterpoint arrived in Hong Kong: 500 free hardware security keys from Yubico, a Silicon Valley–based company, were delivered to pro-democracy journalists and protesters, according to the pro-democracy Hong Kong site Stand News. Cybersecurity experts consider these tools to be among the most effective defenses against hackers targeting online accounts.
The purpose: “Yes, keys were shipped,” Yubico spokesperson Ashton Tupper says. “Yubico has a long-standing mission to ensure that people at high risk are protected online. The company works with many nonprofit organizations dedicated to an open internet and free speech.”
Yubico has a track record of working with journalists to protect their cybersecurity. That kind of relationship is increasingly common. Tech companies like Google and FireEye have their own outreach programs to help protect journalists and others; I’ve received several keys as part of this work.
The power of security keys: A hardware security key is the strongest form of two-factor authentication an online account can have: unlike other forms of two-factor authentication, a key cannot be imitated or captured by phishing.
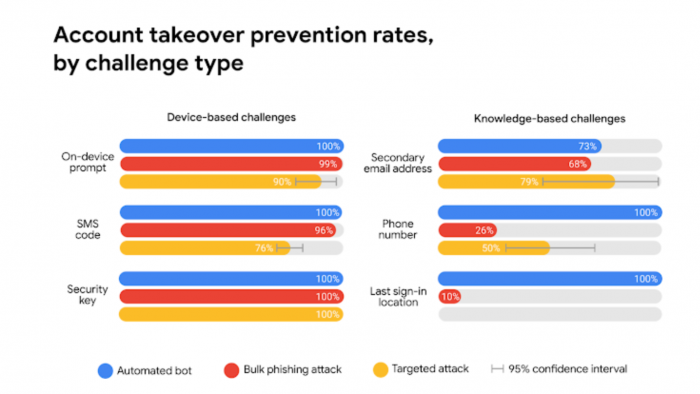
The best way to understand how powerful and important security keys are is to look at the numbers. Google, which sells its own hardware key, published research this year showing that security keys stopping 100% of account takeover attempts. In 2018, Google said that since employees began using security keys the company had not suffered a single account takeover.
The threat: China is one of the world’s most powerful actors in cyberspace. Hong Kong is a sensitive hot spot because of a pro-democracy movement resisting Beijing’s attempts to exert greater control over the semi-autonomous region.
Journalists and protesters in Hong Kong are at risk from a country that’s proved itself more than willing to use cyber tools to go after any group it perceives as an adversary. Most overtly, China is engaging in an information campaign both domestically and around the world in order to push Beijing’s narrative about recent events.
The risk, however, does not end there. As previous campaigns around the world have shown, most famously the Russian operation during the American 2016 election, hacking can be used in concert with information campaigns to accomplish geopolitical goals.
Deep Dive
Computing
Inside the hunt for new physics at the world’s largest particle collider
The Large Hadron Collider hasn’t seen any new particles since the discovery of the Higgs boson in 2012. Here’s what researchers are trying to do about it.
How ASML took over the chipmaking chessboard
MIT Technology Review sat down with outgoing CTO Martin van den Brink to talk about the company’s rise to dominance and the life and death of Moore’s Law.
How Wi-Fi sensing became usable tech
After a decade of obscurity, the technology is being used to track people’s movements.
Algorithms are everywhere
Three new books warn against turning into the person the algorithm thinks you are.
Stay connected
Get the latest updates from
MIT Technology Review
Discover special offers, top stories, upcoming events, and more.